Deep and Dark Web
What is the Deep Web?
The world wide web (commonly called “the web”) is an information retrieval service that allows users to access web pages hosted on the Internet by typing an IP address or URL into a web browser application on a connected device.
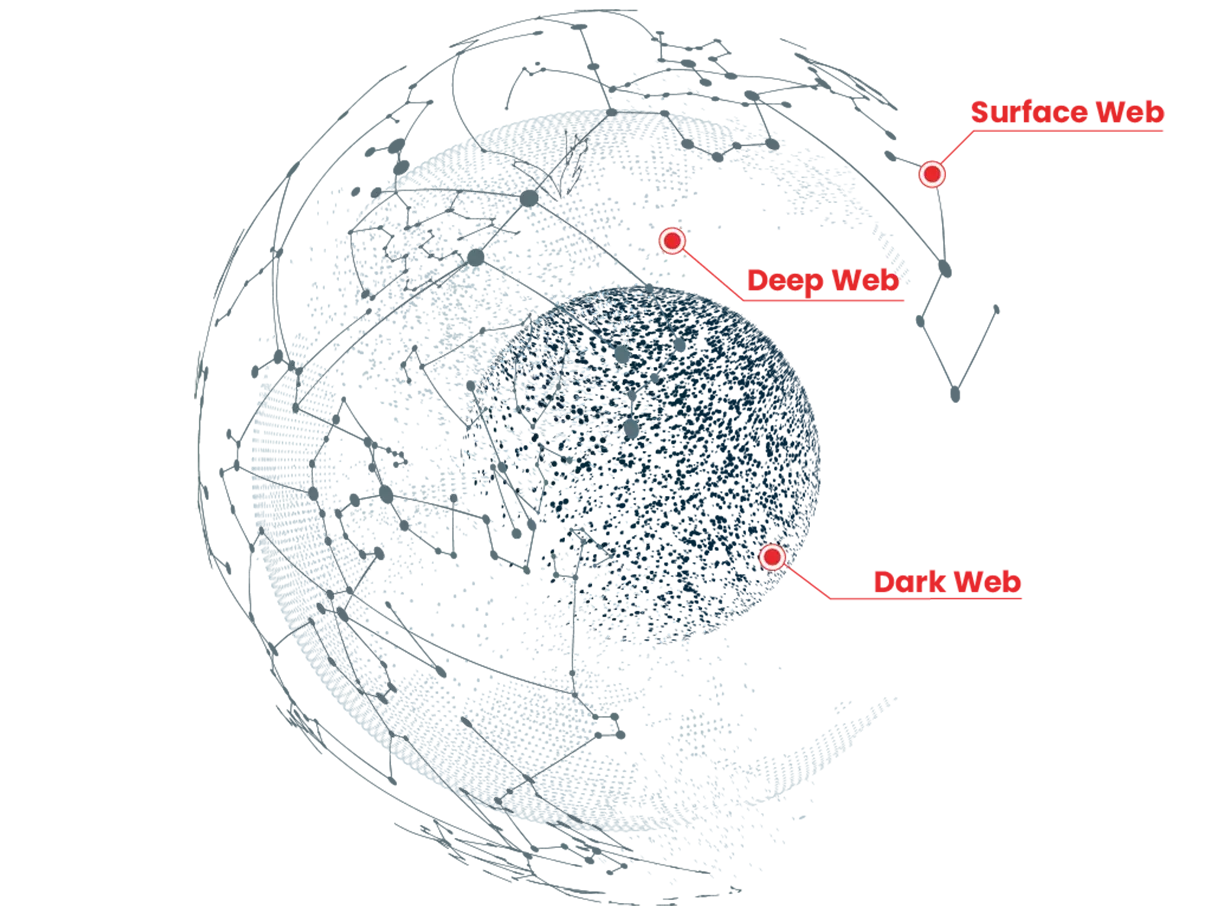
The collection of web pages that have been crawled and indexed by search engines is known as the Surface Web (or the Indexed Web, or Visible Web). These web pages are freely accessible to the public using the most common web browser applications like Safari, Google Chrome, and Mozilla Firefox. Just 5% of all websites appear on the surface web (Kaspersky).
In contrast, the Deep Web is the collection of web pages that are not indexed by search engines and do not appear in the search results of engines like Google and Bing. To access a page on the Deep Web, users must have prior knowledge of its IP address or URL. Pages on the deep web can still be accessed using traditional web browsers.
Content on the deep web includes private intranets, private member sites, public and private databases, and many other types of hidden content. Most of this content is completely legal and may even be used to power applications and services we interact with on a daily basis – it just isn’t meant to be searchable by the public. All password-protected content is part of the deep web, including financial accounts, secure databases, webmail accounts, and subscription websites.
Cybercriminals may attempt to avoid detection by hosting malicious domains and other fraudulent digital assets in the deep web where they won’t be discovered by search engines or other web crawler applications.
What is the Dark Web?
The Dark Web, also known as the Invisible Web, or Hidden Web, is a collection of web pages that don’t appear on search engines and can only be accessed using web browsers with specialized features for encrypting data and enforcing user anonymity.
The essential components of the Dark Web are:
- Anonymized Browsers – Web pages on the Dark Web block access for web browsers that collect data from user sessions, such as Safari and Google Chrome. They can only be accessed using browsers that enforce user anonymity, such as the TOR browser, Whonix, and The Amnesic Incognito Live System (TAILS).
- Encryption Techniques – Dark web browsers use powerful encryption technologies to secure data in transit and protect user identity.
- Virtual Private Networks (VPNs) – A VPN uses the Internet to create a secure, private data tunnel from the user’s device to a remote server. Cybercriminals use VPNs to hide their location when accessing the dark web.
- Routing Algorithms – Random routing algorithms are also used to disguise the user’s location. The user’s Internet connection is bounced through a series of relays that make it nearly impossible to trace back to its origin.
The anonymity offered by these browsers makes activity on the dark web virtually untraceable. As a result, the dark web has become a hotbed for illicit activity. Cybercriminals use the dark web to buy, sell, and trade malware applications, as well as to sell or leak stolen data.
Deep Web vs. Dark Web: What’s the Difference?
The Deep Web and Dark Web are both made up of pages that can’t be accessed through traditional search engines.
But while pages on the Deep Web can be accessed using traditional web browsers, those on the Dark Web must be accessed using specialized web browsers that ensure user anonymity.
The ability to interact anonymously has made the Dark Web an attractive venue for illicit websites. One research study crawled the Dark Web and discovered 5,205 live websites – of which 1,547 were determined to be illicit in nature (T&F Online).
Why is Deep and Dark Web Monitoring Important?
A comprehensive cybersecurity monitoring solution should include surveillance of the deep and dark web, both of which may play host to cyberattack infrastructure.
Malicious domains, fraudulent web apps, and spoofed websites are likely to be hosted in the Deep Web, where they can stay hidden from crawlers and search engines but remain accessible to victims using traditional web browsers.
The Dark Web hosts illicit marketplaces where digital threat actors can purchase malware-as-a-service, download exploit kits, or gain access to botnets for use in cybercrime.
Mining both the deep and dark webs for actionable threat intelligence can help enterprise SecOps teams improve their security posture and protect their organizations against cyberattacks that originate in the hidden areas of the web.
How Does ZeroFox Monitor the Deep and Dark Web?
ZeroFox monitors paste sites, hacker forums, hidden communication channels, TOR services, and thousands of other deep and dark web sources to detect, disrupt, and dismantle cyberattack infrastructure.
Check out our virtual panel Keep Your Enemies Close: Playing Offense on the Dark Web to learn how threat actors launch cyberattacks from the Dark Web and what your organization can do to fight back.
Why ZeroFox for Deep & Dark Web Monitoring?
The only cybersecurity company to go public in 2022, ZeroFox protects the world’s leading companies, organizations, and governments with the only unified platform for external cybersecurity.
ZeroFox has over 100 analysts constantly monitoring the Deep & Dark Web
Comprehensive
Proprietary data sets enable extensive analysis, from unique historical data to the latest dark web research from our embedded operatives.
Accurate
Covert chatter-focused feeds alerting on mentions of your people, locations, and brand including communications collected on Discord, Telegram, IRC, and the Dark Web.
Timely
Direct machine-to-machine access to raw and regularly updated ZeroFox intelligence delivers easily consumable threat data, speeding up decisions and providing early warning when every second counts
ZeroFox has 700+ global disruption partners, including the biggest hosts, registrars, and social media platforms