LookingGlass is now part of ZeroFox.
The solutions you know and trust from LookingGlass, now part of ZeroFox.

Expanding visibility and protection across the external attack surface
scoutPRIME
Monitor your attack surface, enriched with threat intelligence, to manage your cyber risk and vulnerabilities.
scoutTHREAT
Create tailored threat actor models to detect and respond to the most relevant threats to your organization.
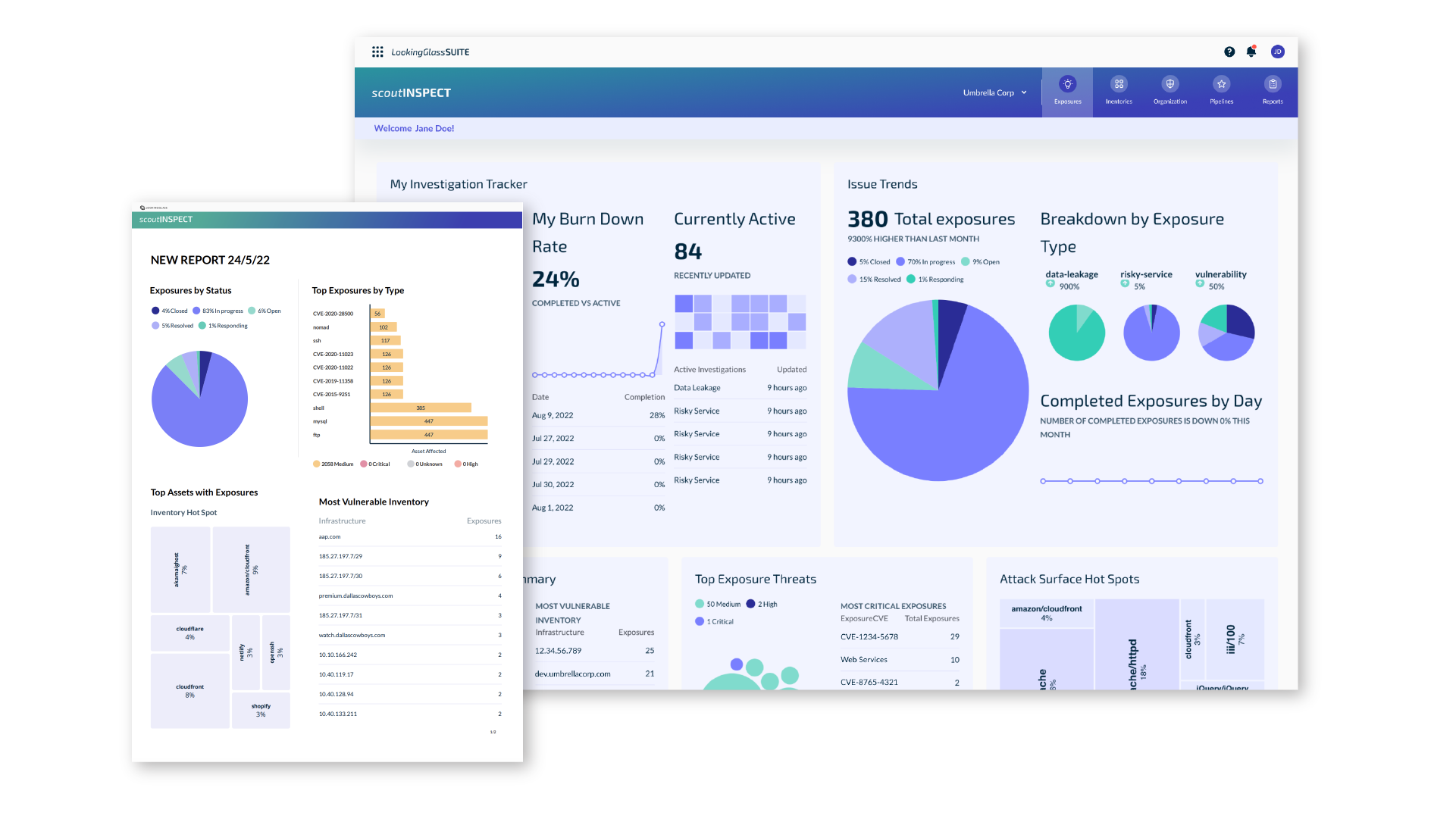
scoutINSPECT
Discover and catalog your assets, validated vulnerabilities and exposures across your external attack surface
scoutPRIME Key Features
DYNAMIC FOOTPRINTING
Create and manage dynamic footprints of any internet-accessible asset or network to identify if an asset on your networks is part of a cyber incident
OUT-OF-THE BOX THREAT INTEL AGGREGATION, ENRICHMENT, AND CONTEXTUALIZATION
Aggregate, normalize, and index 88 data sources and cyber threat intelligence feeds — out of the box.
CUSTOMIZED THREAT SCORING
Leverage the proprietary Threat Indicator Confidence™ (TIC) scoring system developed with scoutPRIME’s dynamic foot-printing capabilities overlaid with enriched and contextualized threat intelligence
API & INTEGRATIONS
Export threat intel in a variety of formats to orchestrate your security appliances and improve cyber defenses.
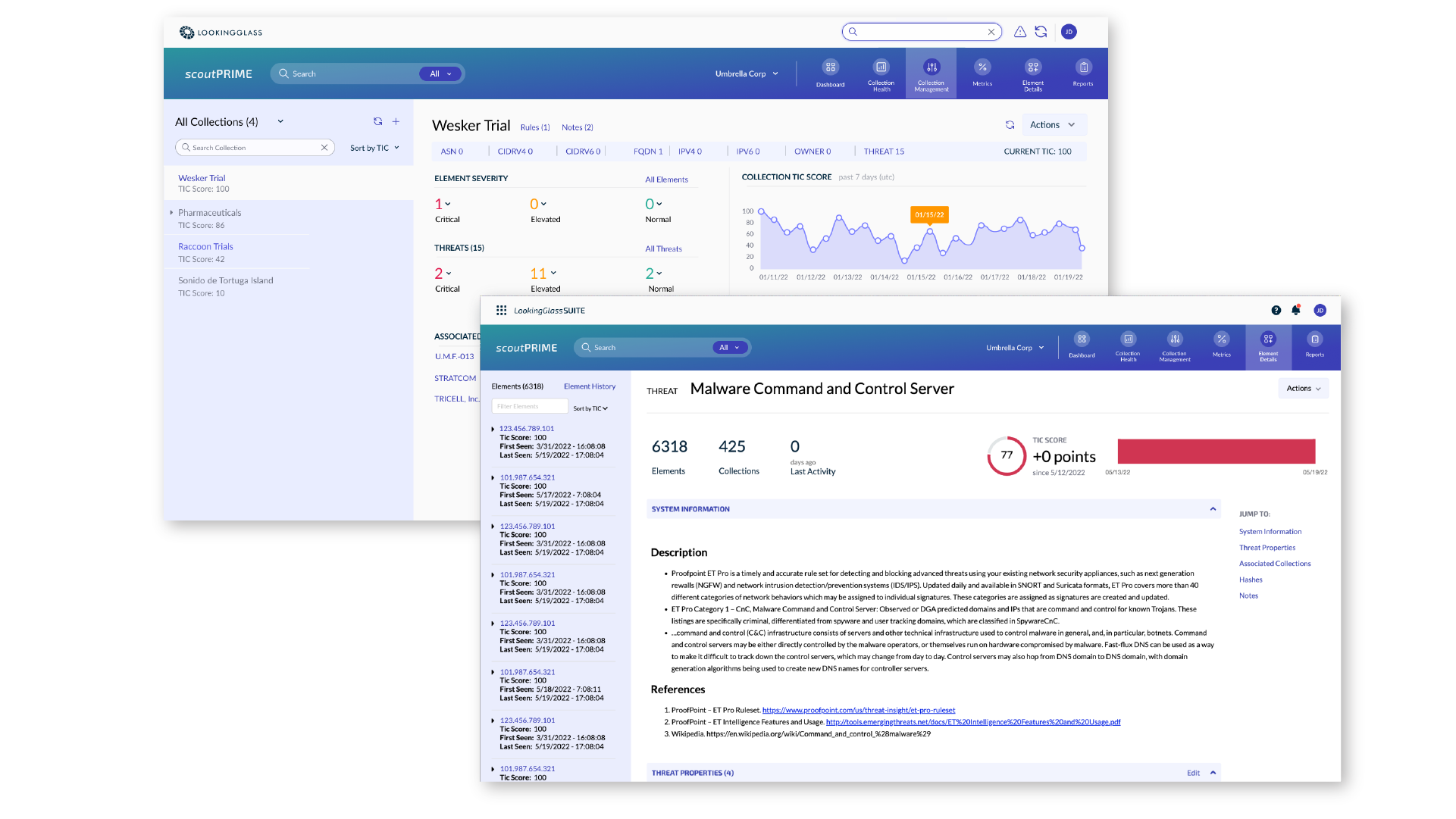
scoutTHREAT Key Features
Anticipate your adversaries’ next move
Quickly pinpoint and understand the threat actors targeting the sectors that matter to your organization and uncover those actors’ capabilities to identify their next move.
Reduce risk and prioritize cyber investment In-Line Remediation
Actor modeling combined with built-in risk scoring enables your organization to highlight key risks and gaps in your security posture and to prioritize cyber investments to mitigate and reduce those risks.
Automate threat indicator and entity extraction
Automatically extract key attack indicators from both structured and unstructured threat intelligence for rapid correlation and processing
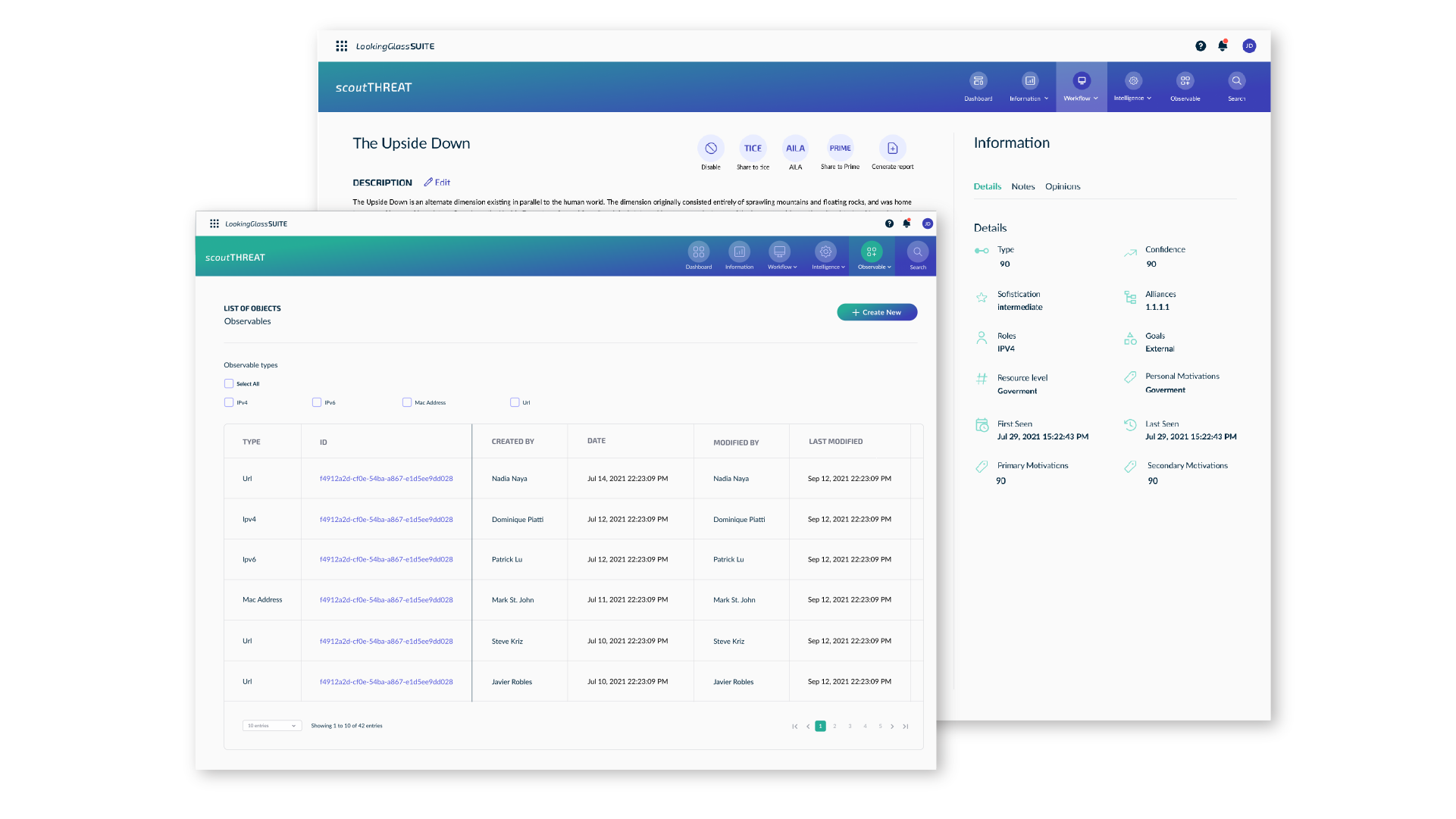
scoutINSPECT Key Features
Inventory Discovery & Mapping
Map your domain infrastructure and sub-domains, and continuously survey your networks to catalog all your internet-facing inventory.
Vulnerability, Exposure, and Misconfiguration Details
Gain deep insight into traditional vulnerabilities and exposures, as well as insight into misconfigurations and changes in inventory
Flexible API and Integrations
Import and export exposures, inventory and intelligence-enriched data in a variety of formats to orchestrate your security appliances and improve cyber defenses.
Explore ZeroFox’s Complete External Cybersecurity Platform
Only the ZeroFox unified External Cybersecurity platform combines the power of AI, full-spectrum intelligence services, and a robust portfolio of breach, incident and takedown response capabilities.

Protection
Protection
Protect brands, domains, executives, and other external assets across the surface, deep, and dark web. Identity and remediate attacks including impersonations, phishing, fraud, account takeover and data leakage at scale.
Learn More
Intelligence
Intelligence
Limit the time and resources spent analyzing and addressing threats. ZeroFox’s team of 200+ threat analysts speak over 27 languages and conduct analysis, research and vulnerability assessment at a global and individual scale.
Learn More
Disruption
Disruption
Reduce time to action on critical threats, including removing fake accounts, websites and posts, and block access to attacker infrastructure. ZeroFox’s disruption and takedown services and Global Disruption Network quickly thwart threats and future attacks.
Learn More