Dark Web Monitoring
Gain powerful visibility into dark web communications to surface data leaks and attack planning with ZeroFox Dark Web Monitoring

What is Dark Web Monitoring?
Data brokers and malicious actors continually sell and trade information on the dark web, and security teams alone are often unable to access forums and marketplaces where your data is likely to be found. Dark web monitoring uses both human and artificial intelligence to collect and analyze raw intelligence from across the dark web in real time. Dark web monitoring searches the dark web for information about your organization, including leaked or stolen data, compromised or breached credentials, intellectual property, and other sensitive materials.
Why Dark Web Monitoring matters
Monitoring the dark web is a difficult and expensive task requiring constant data and intelligence collection across concealed and covert communications platforms. It takes experts who have infiltrated and built relationships within these deep and dark web communities to monitor channels including TOR, I2P, ZeroNet, Telegram, and Discord. This inside information provides organizations with early detection of credential theft and other data leakage; contextual analysis of cyberattacks; and actionable alerts.
Deep and Dark Web Protection
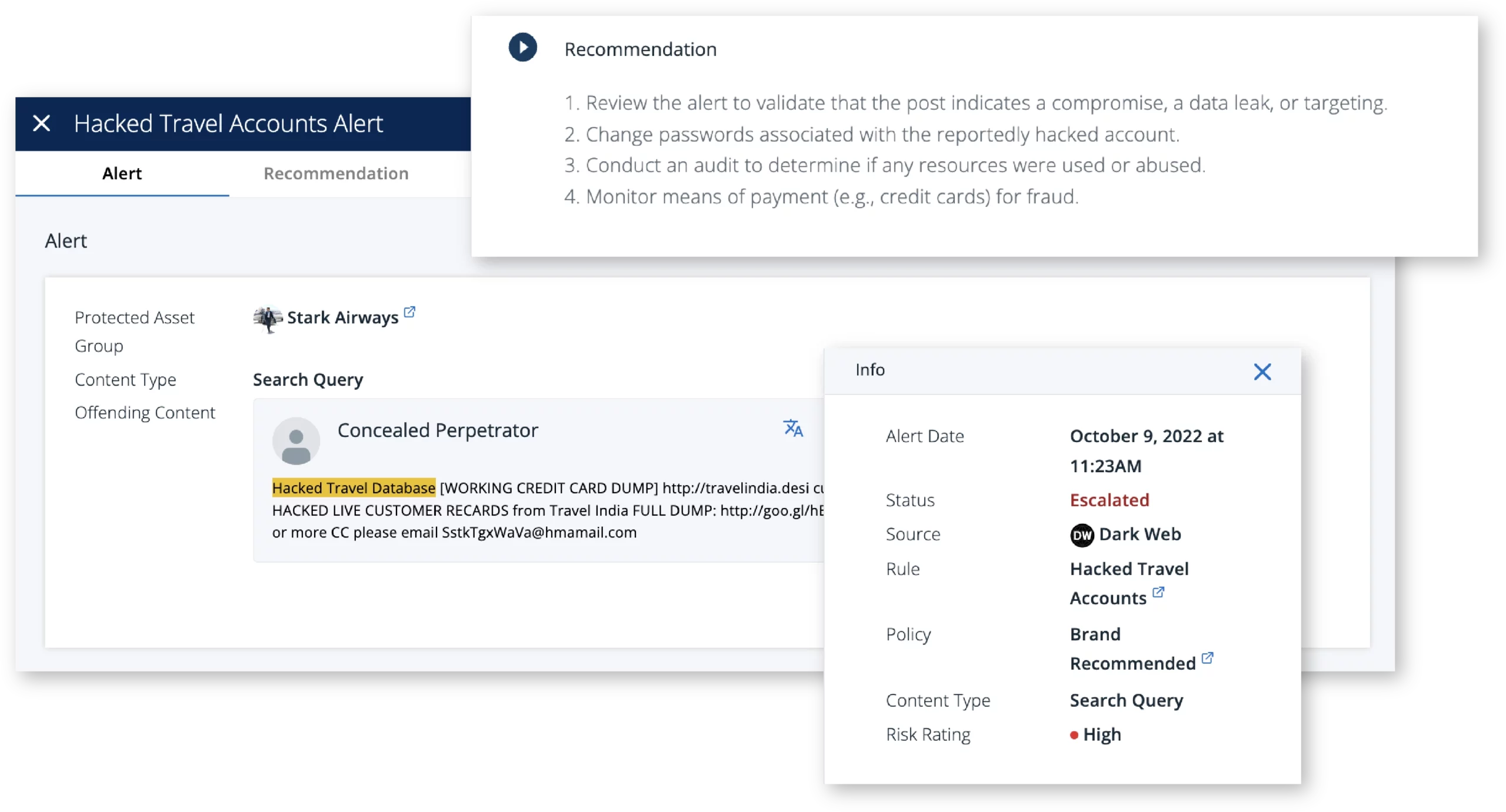
Leverage Dark Web Monitoring to uncover attacks before they happen and find leaked information
Dark Web Monitoring Provides Critical Early Warning.

Comprehensive Alerts that Enable Fast Action.

The ZeroFox Advantage
For Dark Web Monitoring
Provides early warning of information leakage, contextual analysis of cyberattacks, and actionable alerts to keep clients, employees, and brands protected.
How it Works
- Collect intelligence via scraping, API, human collection and other techniques across a broad range of deep and dark web sources including TOR, I2P, ZeroNet, and Paste Sites.01
- Analyze thousands of posts daily across AI classifiers and advanced analysis models such as Natural Language Processing (NLP) to identify leaked data or relevant attack chatter.02
- Assess risks, vulnerabilities and malicious exploitation associated with executives, brands, customers and vendors with expert recommendations to improve security operations.03
- Deliver high-fidelity, SOC-vetted alerts of illegal sharing of customer information, account credentials and PII, or other fraudulent activity.04

Go From Reactive to Proactive with Dark Web Monitoring
Frequently asked questions
ZeroFox Dark Web Monitoring safeguards businesses against data leakage, breaches, and the illegal sale of data on a broad range of deep and dark web sites including TOR, I2P, ZeroNet, and Paste Sites. You’ll be able to detect the sharing of customer information, account credentials, passport numbers, and PII that puts clients, employees, brand, and business at risk. ZeroFox continuously monitors deep and dark web channels to detect and alert teams to information leakage and contextual analysis of cyberattacks.
