External Attack Surface Management
Identify and proactively protect known and unknown internet-facing assets before they can be exploited.

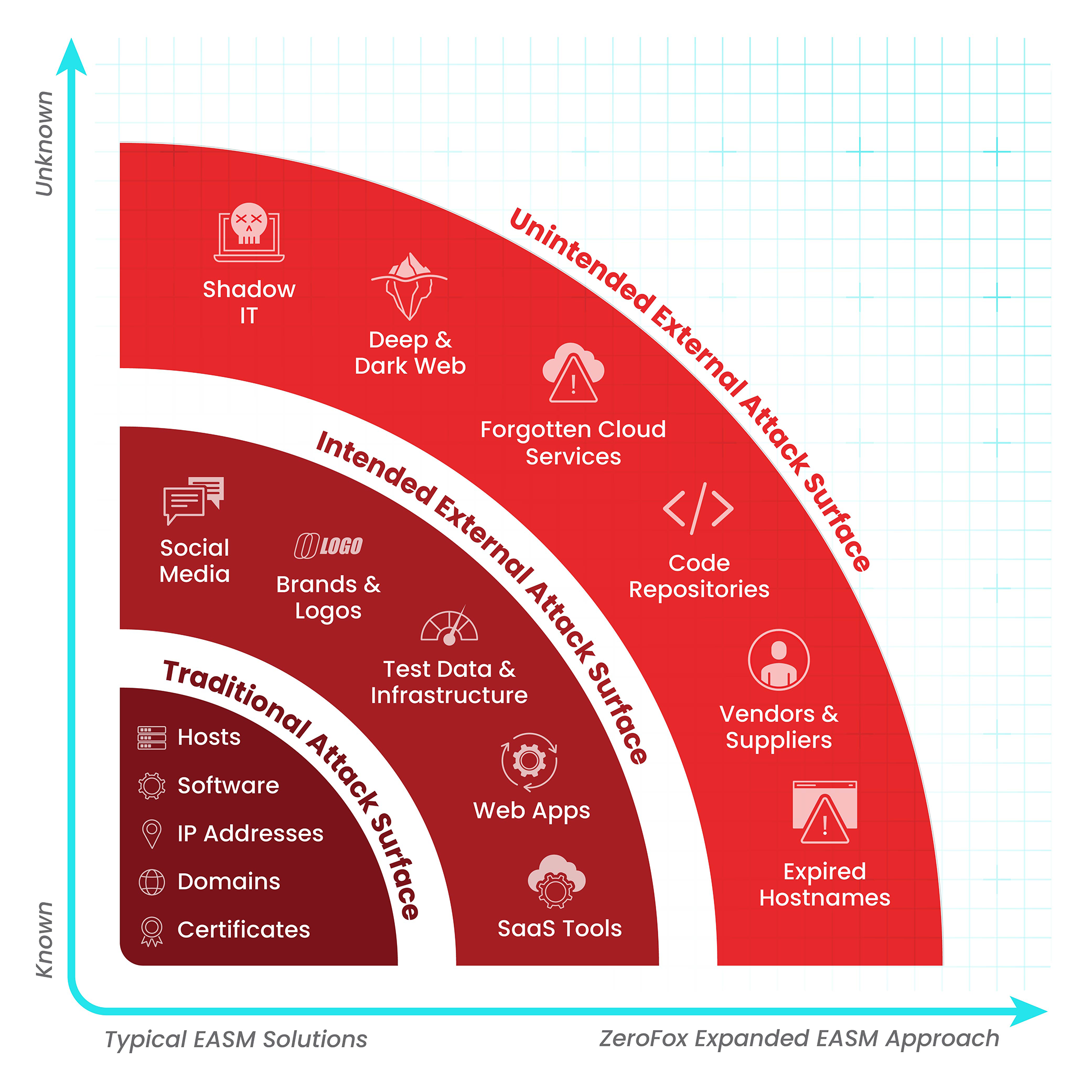
Your External Attack Surface is Bigger and Growing Faster Than You Think It Is
Externally exposed digital assets create a wide attack surface for cybercriminals. Yet most organizations are not fully aware of the constantly changing scope of their internet-facing assets and services. Are you effectively protecting your hidden digital cyber risks?
Common unmonitored and unmanaged exposures include:
- forgotten cloud services
- server misconfigurations
- expired hostnames and weak certificates
- abandoned development and demo projects

Why External Attack Surface Management?
Security teams are stretched thin, constantly responding to security incidents and alerts, leaving assets exposed and ripe for attacker exploitation.
Zerofox External Attack Surface Management
The ZeroFox External Attack Surface Management (EASM) solution defines and maps your organization's internet-exposed attack surface, identifying known and unknown assets. It combines advanced identification techniques with contextual vulnerability intelligence and prioritization capabilities to enable rapid mitigation of potential threats across your digital attack surface.
- Discover and inventory digital assets
- Analyze and prioritize exposures and vulnerabilities
- Combat asset sprawl and shadow IT
- Detect data leakage
- Reduce phishing and social engineering attacks
- Adhere to regulatory compliance requirements
- Visualize your external digital risk from one view
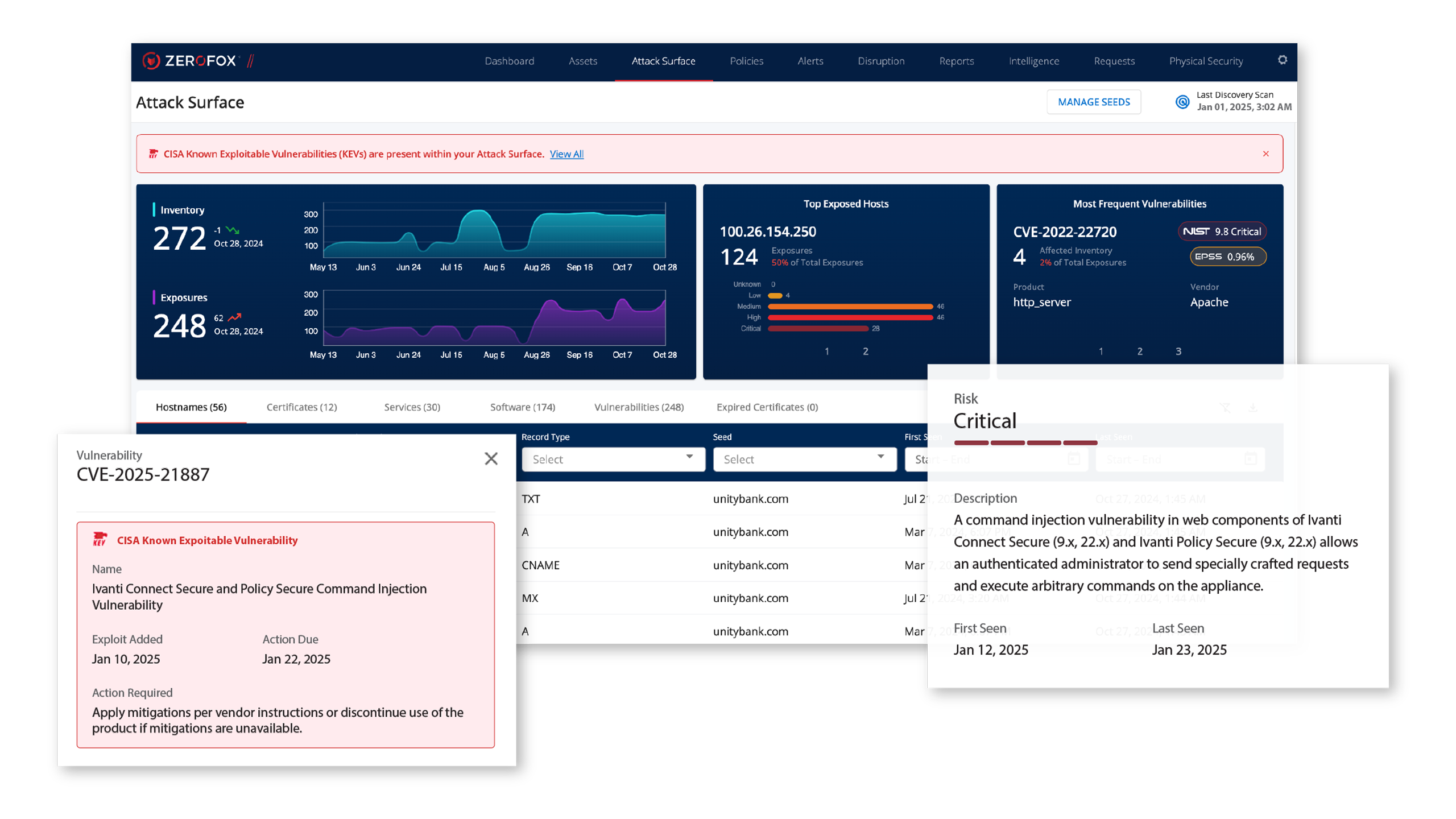
Reduce Your Digital Risk
Discover & Inventory
- Continuously uncover your full digital footprint—including cloud, on-prem, shadow IT, third-party, and even dark web assets.
- Comprehensive Discovery: Identify domains, IP addresses, CIDR blocks, open ports, risky services, security certificates, shadow IT, misconfigurations, code repositories, cloud/CDN providers, and more.
- Visual Mapping: Instantly see asset relationships and exposure chains.
- Attacker-Like Scanning: Detect new assets and risks in real time.
- Embedded Screenshots: Get instant visual context to speed investigations.
Analyze & Prioritize Risk
- Cut through the noise with rich threat context and smart risk scoring.
- Context-Rich Intelligence: Enriched with CVE, CVSS, EPSS, and CISA KEV data.
- Risk-Based Prioritization: Focus on threats based on exploitability, business impact, and real-world activity.
Remediate Faster
- Act quickly with clear, guided remediation and automation support.
- AI-Driven Guidance: Step-by-step AI-based remediation recommendations enable rapid mitigation efforts.
- Reduce MTTD & MTTR: Slash mean time to detect and respond with actionable, prescriptive guidance—empowering your teams to resolve issues before they become incidents.

Cyber Threat Intelligence LeaderZerofox EASM AI-based remediation recommendations blow their competition out of the water, delivering immense value to our organization.
The Intersection of ASM, Cyber-Threat Intelligence, and DRP
To understand how organizations are evolving their approach to attack surface management, cyber-threat intelligence, and digital risk protection, TechTarget’s Enterprise Strategy Group surveyed cybersecurity professionals at organizations. Explore the results and suggestions in this report.

See Why External Attack Surface Management is Critical to Your Holistic External Cybersecurity Program
Frequently asked questions
Digital transformation, hybrid work, and complex software supply chains have all led to an unprecedented expansion of unknown and unmanaged cyber assets, systems, and exposures across the external attack surface. With ZeroFox Attack Surface Management, proactively remove threat actors’ targets of opportunity through full-spectrum discovery and enumeration of internet-facing assets, including subdomains, IP addresses, software, security certificates, Shadow IT, and more. Performing continuous correlation and analysis of exposures with actionable alerting and reporting enables the rapid prioritization of remediation decisions.
