Security On-Demand Investigations
Custom threat intelligence to address critical security questions when you need it.

What are On-Demand Investigations?
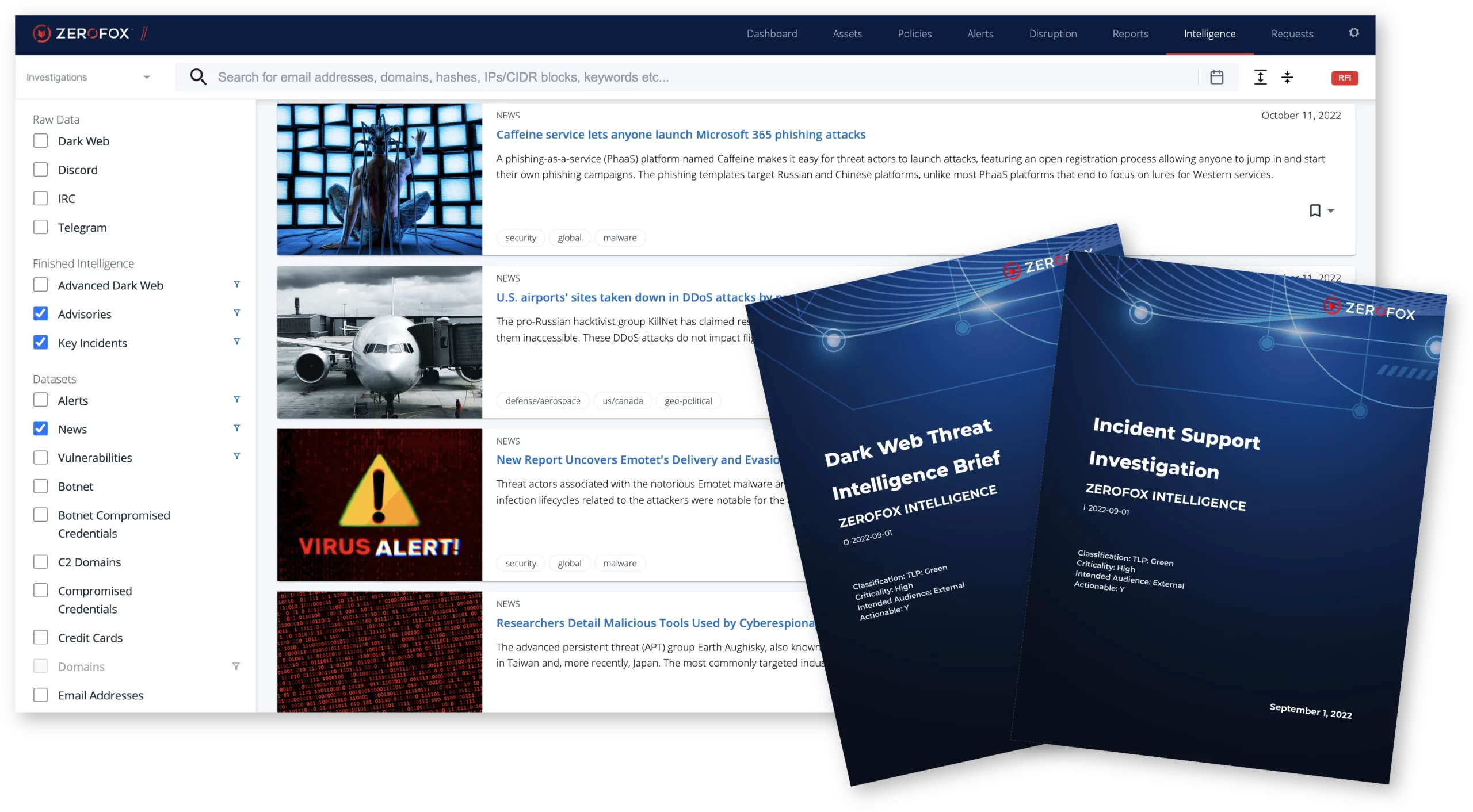
On-Demand Investigations are client-directed projects performed by highly-skilled analysts who deliver finished intelligence reports, technical cybersecurity analysis, threat assessments, research, and ad-hoc analytic projects tailored to your organization. Intelligence analysts conduct in-depth analyses on threat actors, online criminal activity, or third parties; they can assess potential threats to executives and their families; or research a new ransomware strain. Threats change and our analysts adapt to meet the unique needs of our customers.
Why are On-Demand Investigations important?
Organizations don’t have the tools, personnel, or time to keep up with threats to their digital and physical assets. However, they still need the ability to accurately assess the most urgent threats and respond rapidly with confidence. With timely, relevant, and actionable intelligence that answers critical physical, cyber, and geopolitical questions, security teams can improve security decision-making and drive proactive corporate risk strategies.
Why ZeroFox for On-Demand Investigations?
Flexible intelligence capabilities tailored to your needs.
Manage Cyber Threats and Prevent Losses
Leverage fast, practical intelligence to implement countermeasures that prevent operational downtime or the illicit exfiltration of sensitive data.
Discover Adversary Motives & Accelerate Incident Response
Enable SOC teams to bolster organizational resiliency by providing detailed insights around adversarial TTPs.
Free Up Precious Time and Resources
Maximize the efficiency of your security workforce by partnering with ZeroFox to perform important intelligence activities like background checks and third party risk assessments.
Tactical, operational, and strategic intelligence.

The ZeroFox Advantage
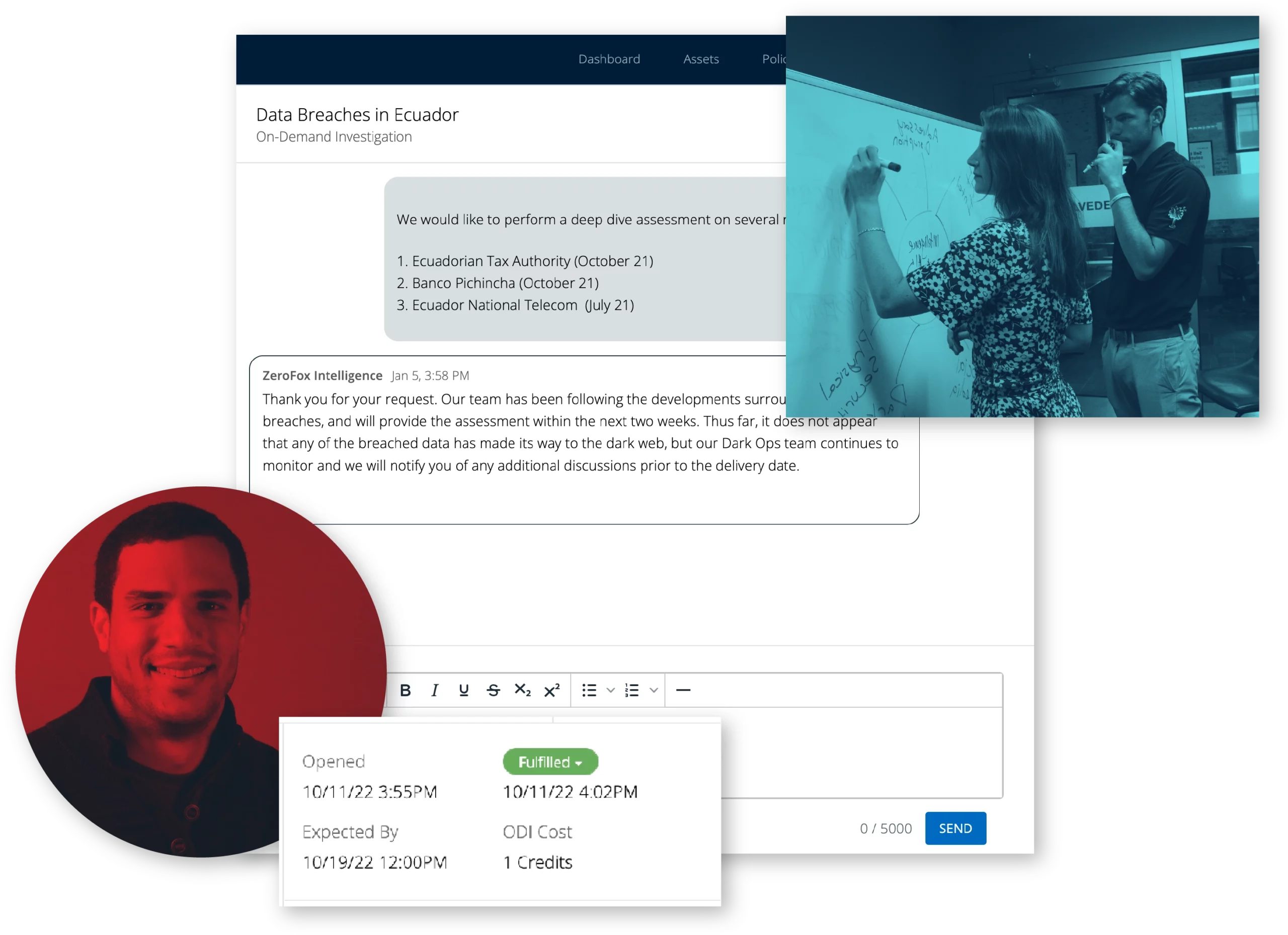
On-Demand Investigations
Responsive team of experts provides tailored intelligence to stay ahead of attackers
How it Works
- Responds to your RFI in a timely and secure manner to scope your project01
- Understands your specific intelligence requirements to ensure you receive relevant and strategic information02
- Researches by collecting global intelligence from within our proprietary data lake, along with other techniques using all relevant OSINT (Surface Web), deep, and dark web sources03
- Produces a tailored finished intelligence report to answer your requirements with key findings and recommendations04
- Delivers intelligence through our secure portal and solicits feedback to ensure your needs have been met05

Access To Actionable Intelligence Can Be Challenging. ZeroFox Can Help.
Frequently asked questions
ZeroFox On-Demand Investigations service provides access to a team of highly skilled intelligence analysts with experience conducting specialized risk assessments, investigations, and threat actor engagement. Additionally, our experts can expand the depth and breadth of your intelligence coverage and help you better understand global physical, cyber, and political risks by applying their intelligence tradecraft and cultural and foreign language skills.
