Universal Takedowns
The undisputed leader in rapidly removing threats at scale across social media, app stores, marketplaces, and domains - powered by automated submissions and a 100% in-house team of experts who pursue, process, and prosecute takedowns on your behalf across virtually every platform.

What are takedowns?
Threat actors rely on fake websites, impersonating social profiles, and malicious content to deceive your customers and damage your brand. Takedowns are the fastest way to shut them down. ZeroFox pairs powerful automation with expert in-house analysts to quickly remove violating domains, social profiles, listings and apps - disrupting scams before they spread and protecting your brand at scale.

Why the world’s best brands trust ZeroFox for takedowns
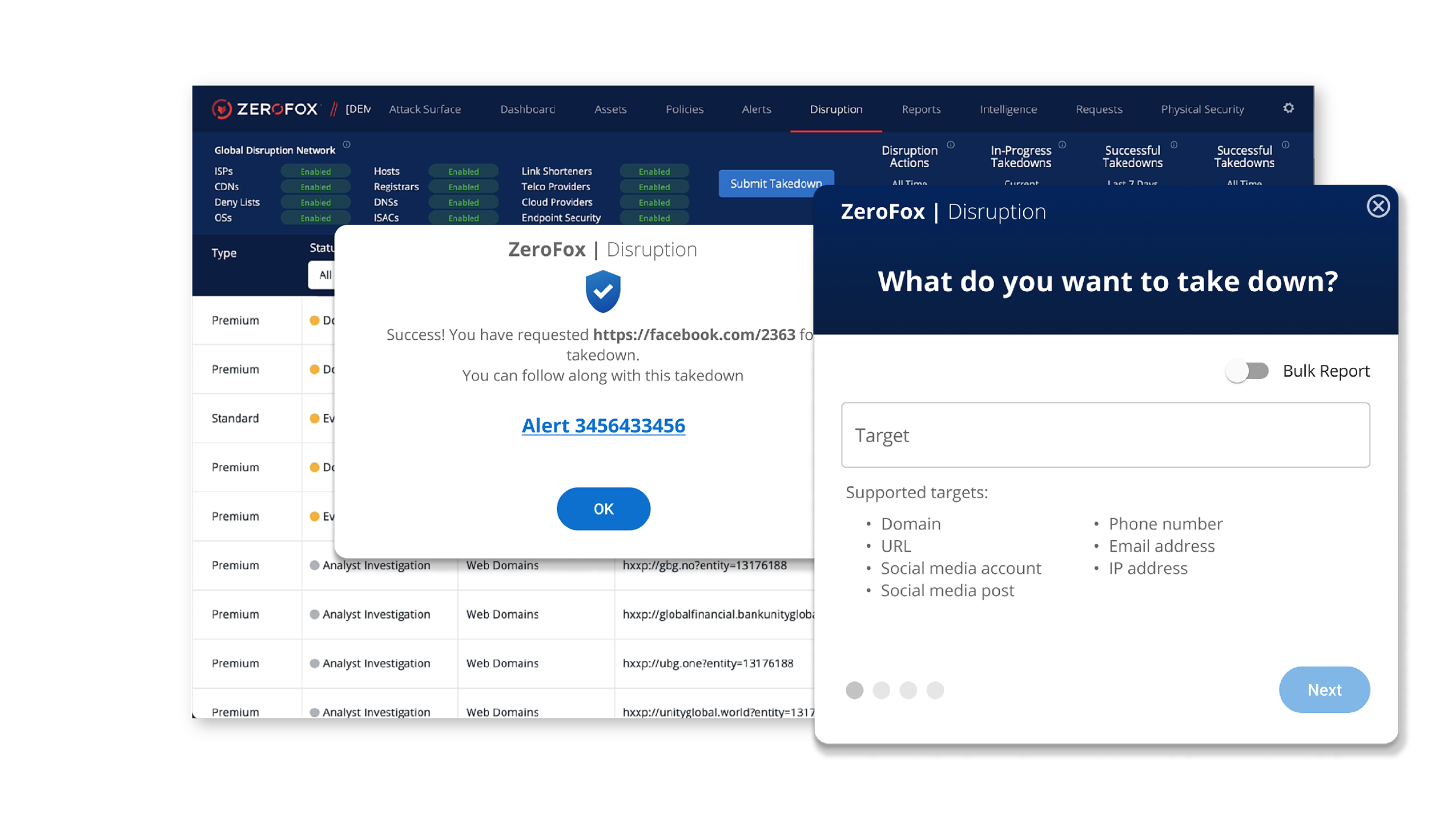
Takedown requests are submitted to ZeroFox
- Malicious domains and URLs
- Impersonating social media accounts
- Fraudulent mobile apps and marketplace listings
- Infringing content, leaked IP and more
ZeroFox rapidly responds
- Submissions are automatically tagged for takedown and sent to the Global Disruption Network
- Automated, proactive blocking actions while takedowns are processing
- Distribution of threat intelligence to common security black lists
Quick threat resolution
- Verification of requests submitted in minutes
- Removal of attacker infrastructure
- Total dashboard visibility through the takedown process
- Transparent reporting, tracking and status updates
Social Media Takedowns
Discover and remove brand, executive, and customer threats
Quickly identify and take down social media threats, such as impersonating accounts, fraud, scams, infringing content, harassment, and more
Gain wide depth and breadth of network coverage
Automate requests and pursue takedowns of violating content across the most widely used global social media networks such as Facebook, Telegram, X (Twitter), Instagram, TikTok, YouTube, LinkedIn, and more
Track every takedown from start to finish
Gain instant visibility into status, activity, screenshots and evidence at-a-glance - no guesswork, no blackouts, complete clarity at every step

Domain Takedowns
Take Action Against Domain Squatters with ZeroFox’s UDRP Solution.
Have a domain dispute that is not takedown eligible but clearly infringes on your brand’s owned trademarks? ZeroFox maintains a 100% success rate working with the World Intellectual Property Organization (WIPO) on your behalf to assess and file Uniform Domain-Name Dispute-Resolution Policy (UDRP) complaints so you can effectively claim ownership and/or remove cybersquat domains.
Want to learn more?
Comprehensive takedown use cases
| Threat Type | Use Case | |
|---|---|---|
| Social Media | Social Media | |
Brand Impersonations & Misuse of IP |
| |
Executive/VIP Impersonations |
| |
Counterfeiting & Piracy |
| |
Fraud & Scams |
| |
Violence, Harassment Misinformation |
| |
| Web Domains | Web Domains | |
Phishing Domains |
| |
Phishing Email Addresses |
| |
IP Infringement |
| |

Why timely takedowns are your most important weapon.
Frequently asked questions
A takedown is the process of removing sites, files and content that violates a host or network’s terms of service (TOS). This is typically achieved when a complainant reports the violation with evidence to the host or network (such as a social media provider or domain registrar) and formally requests its removal or suspension. Every takedown request must adhere to specific guidelines and processes that are unique to the network provider’s own policies. Once a takedown request has been reviewed and accepted by the network provider, the violating content is removed from the internet.